vulnerability
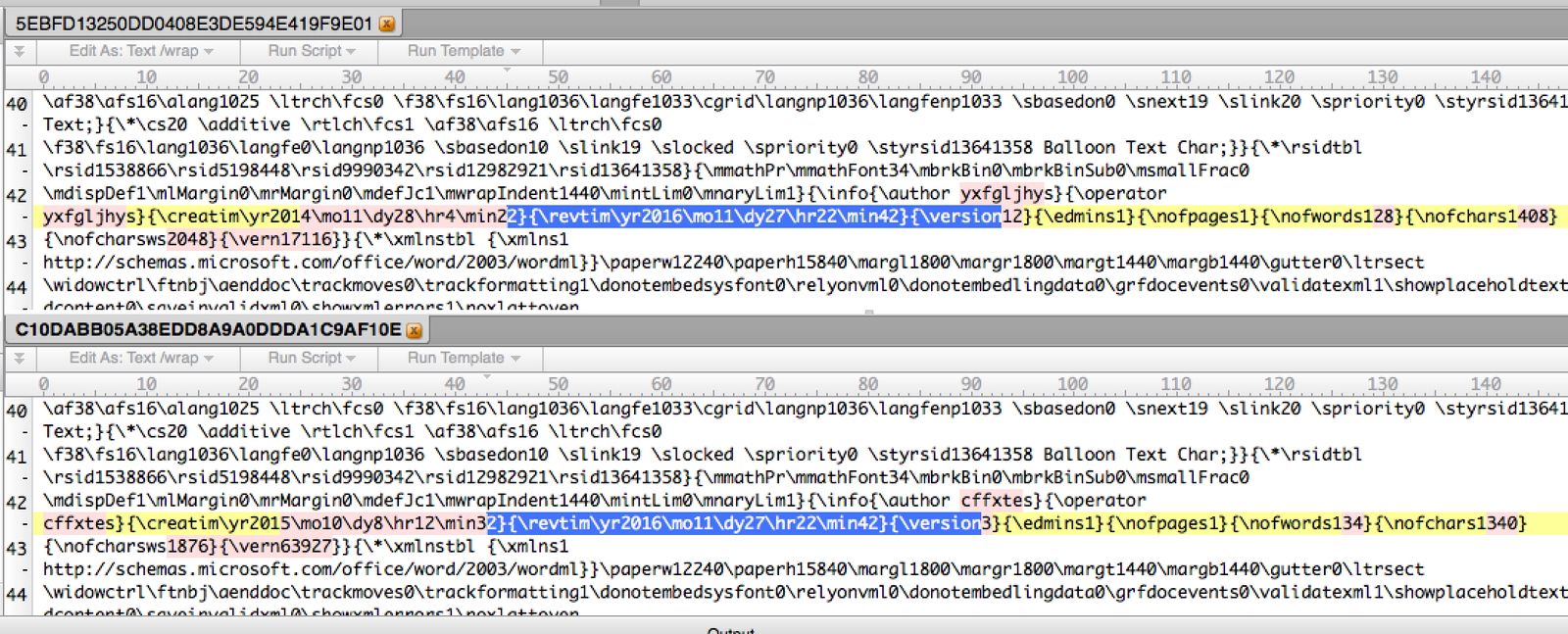
In the spread of Finspy and Latenbot malware for espionage, the same 0day vulnerability was used in Word, and the documents had The same date and time of the last edition
A few days ago, publicly available information about a new 0day-vulnerability in Word (in all versions for all supported operating systems) was published even before the patch was released. It was reported that the vulnerability allows you to quietly execute arbitrary code on the victim’s computer and install malicious software through the RTF document. Briefly described the mechanism of the malware.
The sophisticated nature of the attack and the use of 0day in a popular product hinted that the vulnerability was purposefully used against important targets, and the attack itself was carried out by hackers close to the special services and state structures. And so it happened.
Recall that the first attack using this 0day in January this year. If the protected mode of Office Protected View is disabled in Microsoft Word, then the exploit is automatically launched when the document is opened. After that, the winword.exe process makes an HTTP request to the remote server, from where it downloads an HTA file (an HTML application) disguised as an RTF document. The HTA file automatically launches and executes a malicious script.

This script closes the original infected Word file, and instead shows the user a dummy text document. The original winword.exe process closes to hide the window that OLE2Link displays from the user.

At the same time, the script downloads additional malicious code from the remote server for installation on the computer. Using the .hta implementation, the authors of the exploit effectively bypasses all the memory protection measures implemented in Microsoft, as well as anti-virus protection and most other protection methods.
Immediately say the main thing.
First, The vulnerability has already been assigned the number by classifier: CVE-2017-0199.
Second, Microsoft finally released patches for MS Office 2007, 2010, 2010, 2013 and Windows Vista, 7, Server 2008, Server 2012.
Now FireEye specialists have laid out a more detailed technical analysis in two parts (1, 2), so that some details begin to clear up.
] FireEye published information about two documents that attackers used to attack.
FireEye has information that the vulnerability CVE-2017-0199 was used for state espionage. This 0day was used in attacks with the delivery of old known malware Finspy and Latenbot in January and March 2017, and the last attack of Dridex began after the disclosure of the vulnerability information on April 7. But the similarity between the implementation of these three attacks indicates that their organizers have received the code from a single source, writes FireEye.
The very first of the three attacks was the Finspy attack, first discovered on January 25, 2017. During the attack, a Russian-language document was distributed, allegedly for the authorship of the Ministry of Defense of the Russian Federation and published in the Donetsk People’s Republic. The document is called “Sputnik Sputnik”.

When the SATELLITE DEVELOPER document was opened.doc (MD5: c10dabb05a38edd8a9a0ddda1c9af10e), an exploit was launched that already downloaded the payload from the IP address 95.141.38.110, including the Trojan Finspy. He had universal functionality: searching for documents on the disc, listening to Skype conversations, etc. In addition to the Trojan, a dummy document was downloaded that was shown to the victim instead of the original one.
FireEye could not determine the target of the attack, but the company emphasizes, That the tool Finspy was sold by the corporation Gamma Group to customers from different countries. At the same time, almost simultaneously a 0day-vulnerability was used to spread the Latentbot malware. The organizers of both attacks received the code, probably from a single source, as indicated by the same date and time of the latest edition of the malicious documents that were used in both campaigns: 2016-11-27 22:42:00 (see screenshot at the beginning of the article).
After the information about 0day fell into open access, someone started a spam campaign, spreading the infected documents in large quantities. In this case, malicious Dridex is installed on infected computers. The spam campaign continues to the present day, so do not be surprised if you receive a letter with an attachment in RTF or DOC format (there will still be an RTF document inside).









