Botnet

IBM X-Force employees discovered a variant of the Trojan ELF Linux / Mirai, which is equipped with a new module for bitcoin mining. As before, a worm with worm functionality searches for and infects vulnerable devices with Linux operating system connected to the Internet bitnet: digital video recorders, set-top boxes, video surveillance cameras, IP cameras and routers.
Botnet Mirai began mining bitcoins on DVR and video cameras / Geektimes However, to conduct a profitable DDoS attack, you need to find a customer or a suitable victim who will agree to pay money for stopping the attack (the service is positioned as consulting in the field of information security, protection from DDoS, you can conclude an agreement). Finding clients and victims for an attack is a constant job that takes a lot of time. On the other hand, mining of bitcoins gives a constant passive income and does not require any effort.
It’s unlikely that hackers will earn a lot of money on mining. Even hundreds of thousands of set-top boxes and surveillance cameras can not cheat any significant number of hashes. The owners of the botnet will earn a few Satoshi. But even a few Satoshi are better than nothing, because the botnet is still idle.
On Internet devices, a hasht is simply ludicrous. No one even measured it. It is known that on the Cortex-A8 processors the hashed is 0.12-0.2 Mheshs / s, and on Cortex-A9 – 0.57 Mhesha / s. On most set-top boxes the processors are weaker.
Recall that the worm and botnet Mirai made a lot of noise in September-October 2016. Due to the fact that the worm automatically went through standard login-password combinations, it managed to spread to hundreds of thousands of devices (security cameras, routers, digital set-top boxes and DVR), from which it organized several DDoS attacks. The power of these attacks far exceeded the capabilities of standard botnets from PCs, because conventional computers are much more difficult to infect in such numbers.
One of the first victims of the Mirai botnet in September of last year was journalist Brian Krebs, who specializes in information security topics and Deanonimization of hackers. The traffic to its provider in its peak reached 665 Gbps, which was one of the most powerful DDoS attacks in the history of the Internet. Brian had to move the site offline, because Akamai brought the site out of DDoS-protection, so as not to jeopardize its other customers.
In September-October 2016, the botnet was used to attack the French hosting provider OVH and for a powerful DDoS attack on Dyn, which provides network infrastructure and DNS services for key US organizations. In this case, the flow of garbage requests from tens of millions of IP addresses was about 1 Tb / s. Users around the world had problems accessing the sites of Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix and others. In fact, the Mirai botnet temporarily “put” a small segment of the American Internet.
In November, a new version of Mirai attacked several models of Zyxel and Speedport routers from users of the German Internet provider Deutsche Telekom. As the investigation of Kaspersky Lab showed, the modified version of the worm in this case used a new method of distribution – through the specialized protocol TR-064, which is used by providers for remote management of user devices. In the event that the management interface (on port 7547) is accessible from the outside, it becomes possible either to load and execute arbitrary code on the device, or to do the same, but through the stage of opening access to the traditional web interface.
The web console of the dropper Mirai. Screenshot: IBM X-Force
In September-October 2016, a real war broke out between the hackers for controlling the Mirai botnet after a vulnerability was found in the worm’s code. Although Brian Krebs eventually managed to deanonize the authors of the original version of Mirai, it is very likely that now control of the botnet belongs to other hackers – one or more groupings.
A new version of Mirai with a built-in miner probably belongs to one of those Groupings that are fighting for control of the botnet. The activity of this version of the malware was noted for several days at the end of March.
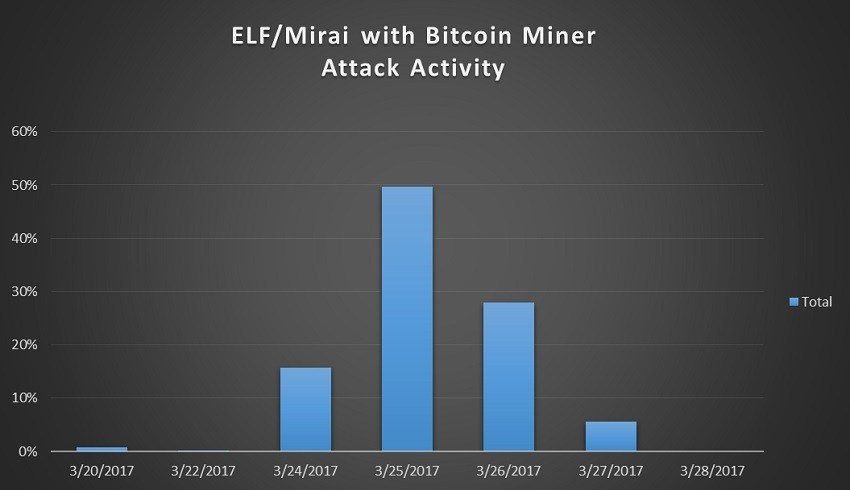
It is reported that the worm is spreading the old methods: scanning the address space in search of new devices that work on Telnet ( Port 23), and selecting passwords for them. Dangers are susceptible to devices under Linux with all versions of BusyBox and DVRHelper, if they have standard passwords installed.








