Samsung

Representative of the ravenous raven of Weeping AngelsFans of the science fiction series “Doctor Who” perfectly remember the alien race of predators. Angels (Weeping Angels). These are the characters of the episode “Do not blink” – the tenth episode of the third season (2007) and one of the best episodes in the history of “Doctor Who.”
From the point of view of an outsider, the Angels look like stone statues whose eyes are often covered with palms . But if you blink while looking at the Angel, you will immediately notice the elusive change in the position of the statue – it seemed to get closer. And God forbid to look away for a long time.

If you look away, the Crying Angel will come close. The fact is that these aliens move only when nobody is looking at them, even if they just blink. In a sense, they are similar to the character of the Greek myths of Gorgon Medusa, which made every person who looks at it stare. Only here this principle operates on the contrary.

Gorgon Medusa, one of the three sisters gorgon (picture of Caravaggio). According to legend, it was a girl with beautiful hair, but god Poseidon took her in the temple of Athena, where an innocent beauty tried to hide from the persecution of God. In retaliation for sacrilege in his temple, Athena turned her hair into a hydra
Greek mythology and modern science fiction surprisingly combined in the depths of the secret laboratories of the CIA and MI5, where software is developed for the needs of foreign intelligence. Admirers of modern pop culture, CIA programmers, of course, watched “Doctor Who,” and that series with Weeping Angels. That’s why they gave this a bookmark for Samsung TVs. The TVs that watch the audience are little Weeping Angels, weeping angels, try to just blink or blurt out the excess.
In the published compilation there was a documentation for the Weeping Angel tab for Samsung TVs with built-in microphones and speech recognition (voice control) enabled. This malicious software is created by the CIA development unit for Embedded Development Branch (EDB) embedded systems in conjunction with the British intelligence MI5 / BTSS. The program adds the TV mode ‘Fake-Off’ when the TV looks turned off, but at the same time records conversations in the room and sends them to the CIA web server.
April 21, 2017 Wikileaks published new information on the Weeping tab Angel – detailed user guide for CIA agents. The document is dated February 28, 2014 (pdf). In the technical documentation, the tool is called EXTENDING. As Wikileaks writes, this is the original version of the bookmark, created in the British intelligence service MI5 / BTSS and upgraded to the CIA. Colleagues from the United Kingdom and the United States coordinated their work on this tool and shared their experience by organizing Joint Development Workshops – joint development workshops.
Three dozen pages of the user’s manual set out the following:
- key EXTENDING bookmark functions;
- malware configuration: the Ubuntu 12.10 ISO image is included in the package to create a Linux virtual machine where the encrypted configuration files are generated (the Oracle VM Virtual Box installer allows you to install the environment for running this Ubuntu VM virtual machine) – the configuration generation should To be carried out only on a computer that is secure, disconnected from the Internet; There is also the wlan.bat script for the configuration of the virtual adapter Hosted Network Virtual Adapter on the laptop;
- the installation process;
- compatibility with Samsung TV models;
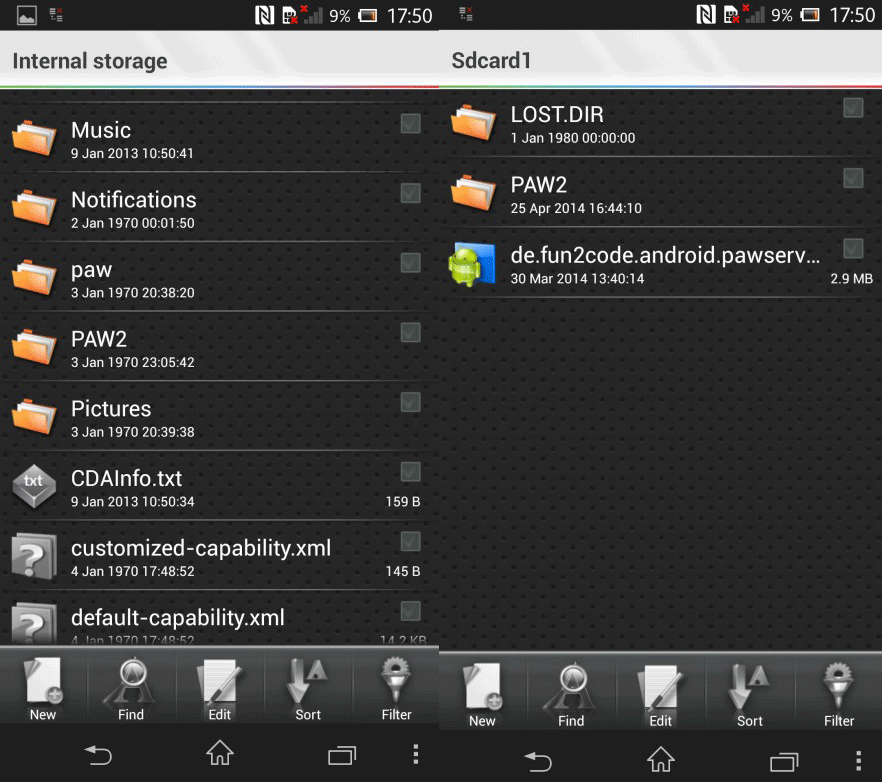
- the process of installing the web server to retrieve information from the TV – the web server is installed using the XAMPP Windows installer, there is also the Android web server PAW Server, the package includes the .apk file and the configured folder PAW2;


- processing of audio data recorded via the built-in microphone using the Windows program ECDLive.exe;
- procedure for deleting a bookmark from the TV (in the original configuration, the “death date” of the bookmark is set);
- testing and possible exploitation problems;
- known problems and bookmarks;
- decoding of error codes (Appendix A).
The document states that the program is designed for the Samsung F Series (firmware 1111, 1112 and 1116), and the preliminary configuration of the malware is performed on a personal computer under Linux. Installation on the TV is carried out with the help of USB-flash drive. The program can work in three modes: 1) permanent audio recording; 2) audio recording only when the TV is off; 3) audio recording only when the TV is on.
As you can see from the documentation, the recorded audio files from the TV are transmitted not via the Internet, but via WiFi – to a laptop or Android-smartphone located nearby. Already it can be connected to the Internet, through it you can get an archive of recorded files or make a wiretap in real time. Probably, this bookmark is best suited for installation on “public” TVs, which are located in office buildings, hotel foyers, cafeterias, hairdressers, etc.
The files of malware from the Vault 7 archive themselves promise to be published after verification And the closure of vulnerabilities by manufacturers.
PS Now the CIA and the FBI are conducting a joint investigation to establish the employee involved in the leakage of documents. It’s amazing that in 1.5 months it was not possible to calculate it.