
Chrome
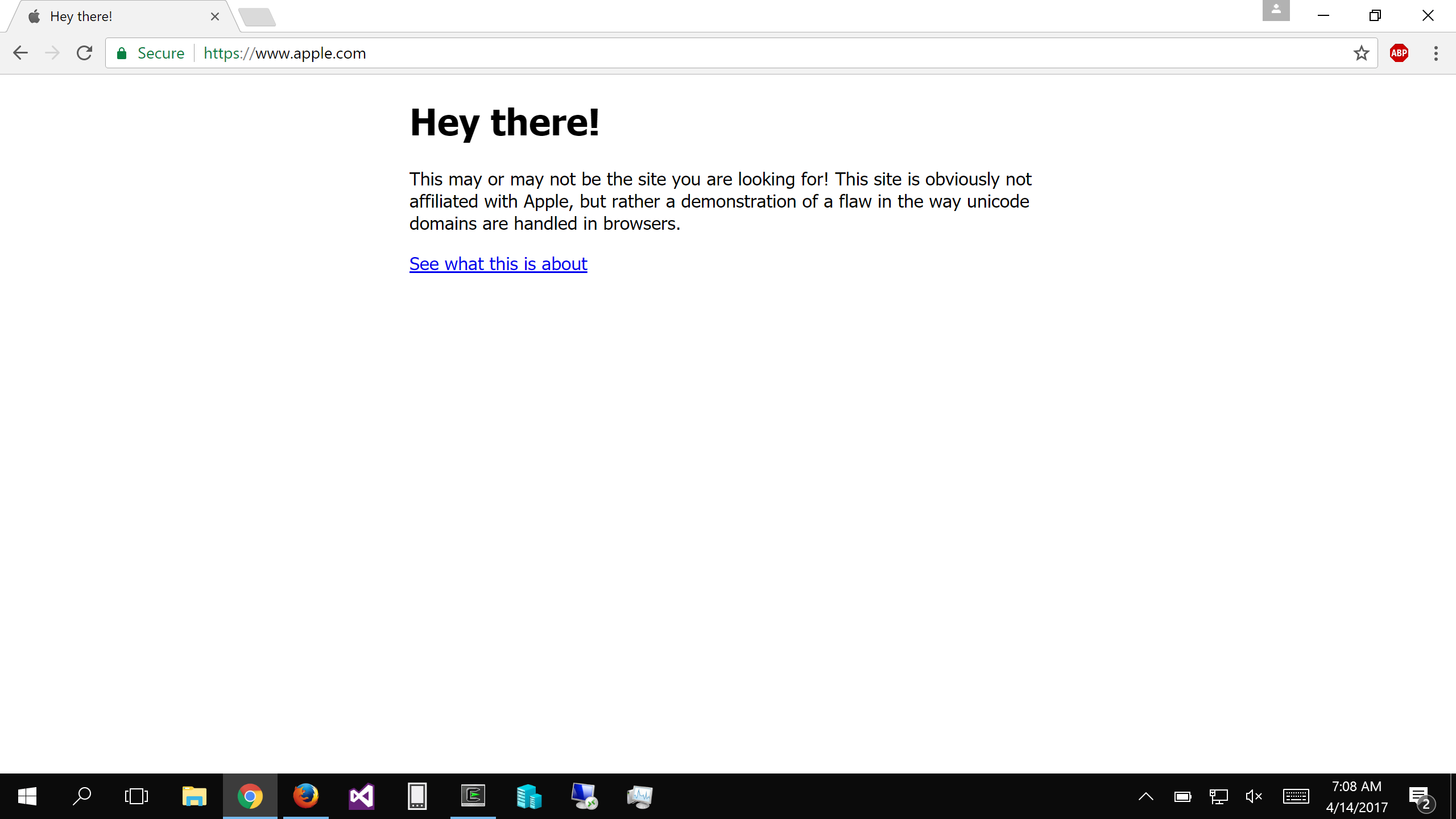
The site https: //www.array.com/ has a true SSL certificate (of course, from Let’s Encrypt) and is marked in the browser as ” Reliable site “. But in fact, this is not what you expected to see. It’s just a demonstration of the concept of chrome- that some modern browsers display site names in Unicode instead of Punycode and mislead users.
Punycode is a way to represent Unicode characters in host names using a limited subset of ASCII. As stated in RFC3492, Punycode is an implementation of the more general Bootstring algorithm, where strings composed of a small set of “base” characters (in this case, ASCII), can represent unique strings composed of a larger set of Unicode characters. For example, the domain 短 .co becomes xn--s7y.co.
In the aforementioned domain https: //www.array.com/, the first letter of the host can be replaced with the Cyrillic symbol “a”, the symbol of the Cyrillic alphabet ( U + 0430), and not ASCII (U + 0041). This is an old kind homographic attack, which developers of browsers and registrars of domain names have long struggled with.
In an ideal world, domain registrars should not register domains that allow homographic attacks, and all browsers will normally display host names in Unicode.
Since the world is not perfect, browser developers have implemented their own methods to combat such attacks. In particular, in Chrome from the 51st version and in Firefox from the 22nd version, the domain version in Unicode will be hidden if characters from different alphabets are mixed in the host. For example, if you replace the first letter with a Cyrillic character in www.array.com, the browsers will show the address “xn--pple-43d.com”.
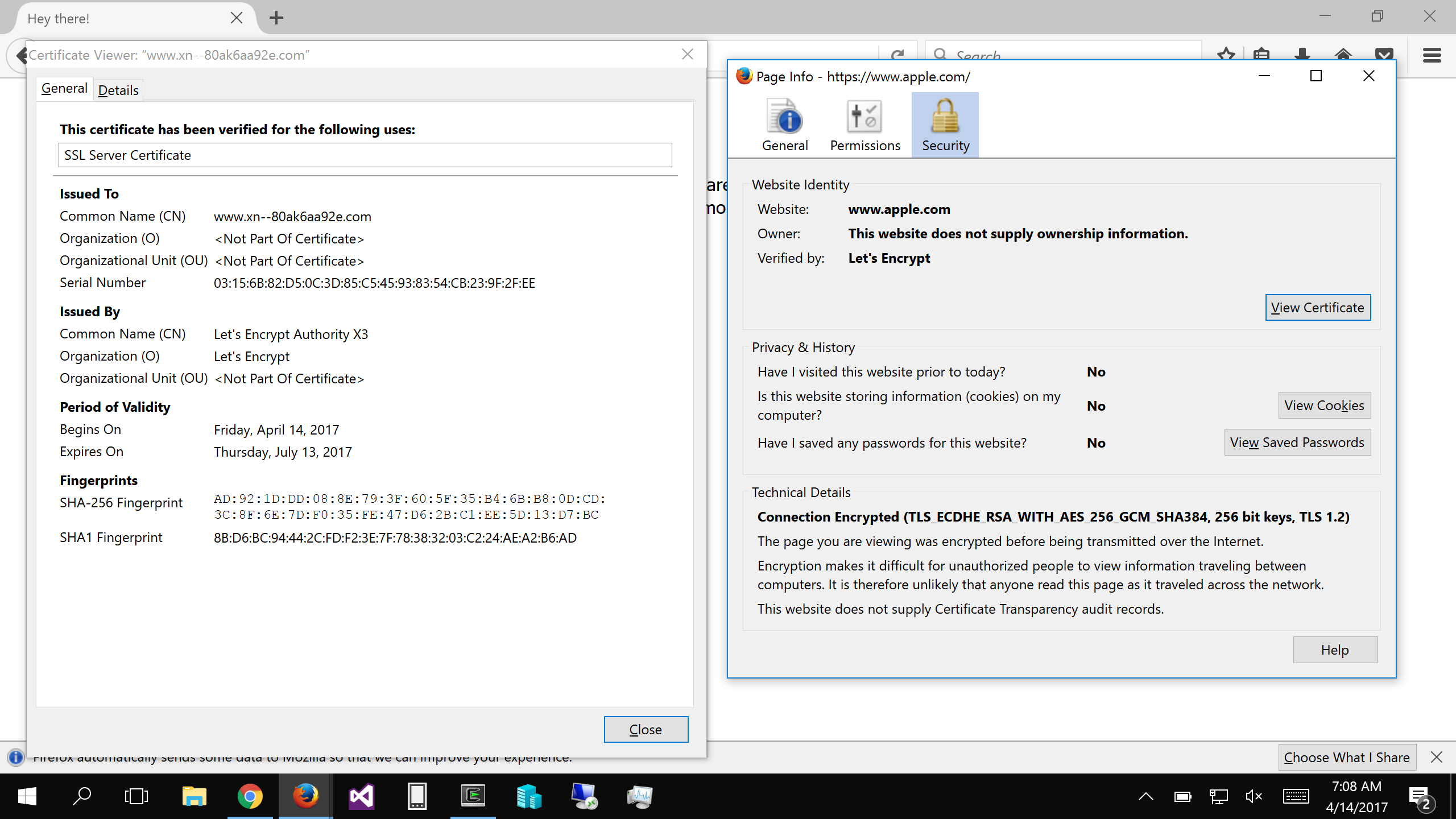
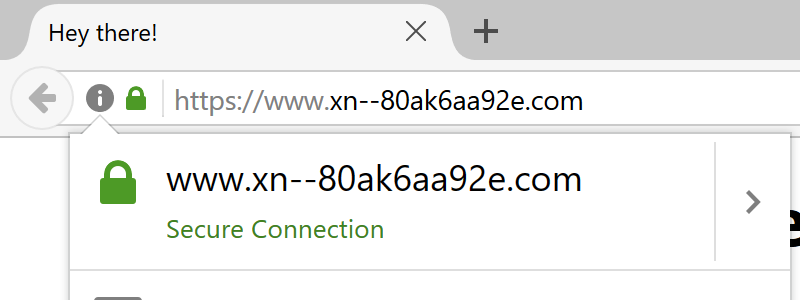
The problem is that this method does not work if the attacker Replaced not a part of the letters, but all letters of the domain to symbols of another alphabet. In the above-mentioned domain of the “apple company” all five characters are replaced with Cyrillic characters. In Punycode, it turns out “xn--80ak6aa92e.com”, but you can see above that the browser does not protect against such an attack.
The faked address is beautifully demonstrated in both Firefox and Chrome of the latest versions. The uppercase Cyrillic “Ӏ” in this font looks exactly like the Latin “l”.
Only if you look at the SSL certificate,
Browsers Internet Explorer and Safari are not affected by this vulnerability. For example, the IE tab immediately displays the name of the site in Punycode.
Fortunately, Chrome developers have prepared a patch that closes this vulnerability. It was originally prepared for the version of Chrome 59, but then decided to include in the composition of Chrome 58, which will be released very soon – April 25. Apparently, after the introduction of this patch, the browser will show the version of Punycode in all “controversial” situations, when there is some probability of phishing, even if the characters belong to the same alphabet. This means that some addresses of Russian sites in Cyrillic, theoretically, will now always be displayed in “ugly” Punycode, and not in “beautiful” Unicode. For example, http: //sahar.com/ will turn into xn-80aa2cbv.com/ .
As for the same patch for Firefox, the situation remains uncertain: the corresponding ticket in Bugzilla was first marked as “closed” and “not executable” (WONTFIX), but now it was reopened . So there is hope that there will be a patch released there as well.
Firefox users only have the opportunity to work around the problem: you can change the setting of network.IDN_show_punycode to true in about: config Setting it to true . Then Firefox will show in the form of Punycode all international IDN domains. Not very elegant, but there is no other option.
Another way to avoid some problems is to use password managers. They will not allow you to enter a saved password on a site that has an address in Punycode that is different from the one stored. Thus, at least you will notice that on the phishing site the saved password is not entered into the form – you can suspect that something is wrong.
In general, you should pay attention to links that are published on web pages or in e-mail messages. There is no such protection, and the addresses of phishing sites can look just like real ones.








