smartphone
Different input methods affect the slope angles, but the neural network recognizes the PIN in any case after data collection by the script
As you know, in any smartphone there are a lot of sensors – GPS, light, orientation sensors, movements and about 20 sensors – they continuously issue data so that the smartphone can interact with the surrounding physical world. Developers have several ways to access information from these sensors, including through a mobile browser, according to the official Javascript API.
It is this method that opens a wide field of possibilities for remote hacking. For example, experts from the School of Informatics at the University of Newcastle developed the script PINlogger.js, through which it is possible to determine through the browser which buttons the user presses on the on-screen keyboard. The script reads information from the tilt sensors of the mobile device each time it is pressed. Surprisingly, in some browsers (Safari) the script running in the browser continues to collect data even from the locked screen. Similarly it works if on the next tab you type the password in online banking without closing the previous tab.
This method is suitable for stealing a PIN-code both through a malicious site with a script, and from any mobile application that has access to information from sensors. The accuracy of recognizing the digits of the PIN is quite high. The four-digit PIN is recognized at the first attempt with a probability of 70%, the second with 86%, the third with 94%, and with the fifth attempt with a probability of 98% for different users or 99% for one user.

The attack vectors from adjacent tabs (b) work only in Chrome and Dolphin for iOS, and the attack from the frame (a) – in all popular browsers, including Safari, Chrome, Firefox, Opera and Dolphin
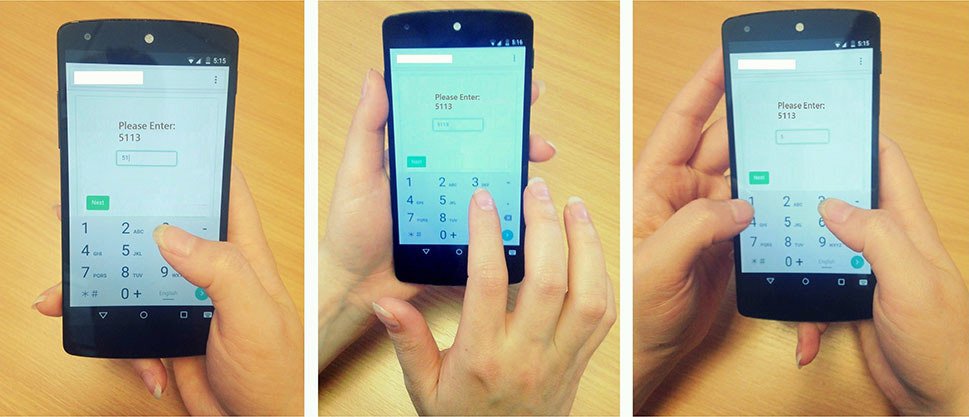
For practical demonstration of the attack, a special interface for entering four-digit PIN-codes was developed. The client part sent to the server the readings of orientation and motion sensors. The server part was implemented on Node.js, and the sensor readings were saved in the MobgoLab database.
In this demonstration, it was easy for researchers to determine the events of keystrokes by using the event onkeydown . The authors of the scientific work draw attention to the fact that a similar approach is used in other programs for assembling PIN-codes according to information from sensors such as TouchLogger and TapLogger. If you want to detect clicks on the locked screen, you may need a more complex segmentation of the sensor data to isolate the desired pieces of data. For example, this can be done by measuring peak signal amplitudes and using additional sensors, as shown in previous scientific papers. The code for data entry is published on GitHub.
The database accumulates information about the sensor pressures and indications at the moment of pressing. Each of the 10 volunteers five times entered 50 four-digit PIN-codes (total 2488 correctly entered PIN-code). This data set was then used to retrieve characteristics and subsequent learning of the neural network (70% of the data was used for training, 15% for testing, and 15% for testing).
Judging by the results of comparative tests, PINlogger.js is much better at recognizing PINs -codes for information from motion sensors than previous similar developments. In addition, it is the first system to steal PIN-codes through the browser, and not through the application installed in the smartphone.

Researchers note that most users do not realize the danger of leakage of personal Data by removing data from sensors. Interrogation of users showed that most of them see a threat in the GPS or in the camera, and not in what is a more real threat – in internal motion sensors, tilt and others. The figure 25 is not accidental: it is the number of sensors counted by researchers in a standard smartphone. The diagram below shows the poll results – in which of the 25 sensors users see the greatest threat.

Users not only do not realize the threat. Many do not even understand what kind of information most of the 25 sensors collect. Some people did not even hear about some sensors.

The problem is that this information is not protected at the operating system level. It is easily accessible for applications, and for any sites through browsers – without permission. Only a few sensors require explicit permission to provide information, including a camera and GPS. The rest provide information quite openly.
With these open data, you can not only collect PIN codes and passwords, but also monitor the user. Any site can determine when a person takes a call and hangs up,

… when a person is sitting, walking or running.

Again, all this information is available to any site and any application without any permission. Security experts and the largest players in the mobile industry are well aware of this, but they have not yet come to a consensus on how to solve it.
Scientific work published 7 April 2017 in the journal International Journal of Information Security (doi: 10.1007 / s10207-017-0369-x), in the public domain.









